Awareness Hints
Information security risk survey for 27001 and TISAX®
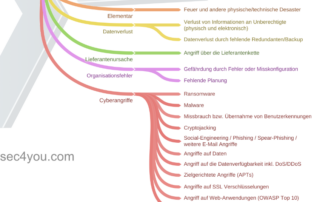
Due to the rapidly increasing threats to an IT operation, every company should survey and evaluate the relevant IT threats with regard to information security. However, the selection of threats for the primary InfoSec protection goals confidentiality, integrity and availability is very complex, because there are no simple threat lists, especially for small and [...]