Jedes Unternehmen sollte aufgrund der rasant steigenden Gefahren für einen IT-Betrieb die relevanten IT-Gefährdungen in Bezug auf die Informationssicherheit erheben und bewerten. Jedoch ist die Auswahl der Gefährdungen (Threats) für die primären InfoSec Schutzziele Vertraulichkeit, Integrität und Verfügbarkeit sehr aufwendig, weil es speziell für kleine und mittelständische Unternehmen keine einfachen Gefährdungslisten gibt.
Dieser Aufgabe hat sich SEC4YOU angenommen und die SEC4YOU Informationssicherheits-Gefährdungsliste 2024 erstellt. In diesem Artikel werden die wichtigsten Bedrohungen vorgestellt und erläutert. Leser bekommen einen fundierten Überblick, gegen welche Gefahren Sie ihr Unternehmen abgesichert haben sollten, da diese mittlerweile fast täglich für Unternehmen zur Realität werden.
Was erreicht man durch eine Informationssicherheitsrisikobeurteilung?
Neben der Vermeidung erheblicher bis existenzbedrohender wirtschaftlicher sowie immaterieller Schäden, unterstützt eine Informationssicherheitsrisikobeurteilung die Auswahl geeigneter InfoSec Maßnahmen, die erforderlich sind, um das Unternehmen vor den jeweiligen Gefahren zu schützen. Sofern Sie ein ISMS nach ISO 27001, TISAX® oder NIS2 betreiben, muss das Unternehmen das komplette Risiko-Assessment von der Risiko-Methode, den Beurteilungskriterien und der Beurteilung dokumentiert nachweisen.
Quellen für Informationssicherheits-Bedrohungen
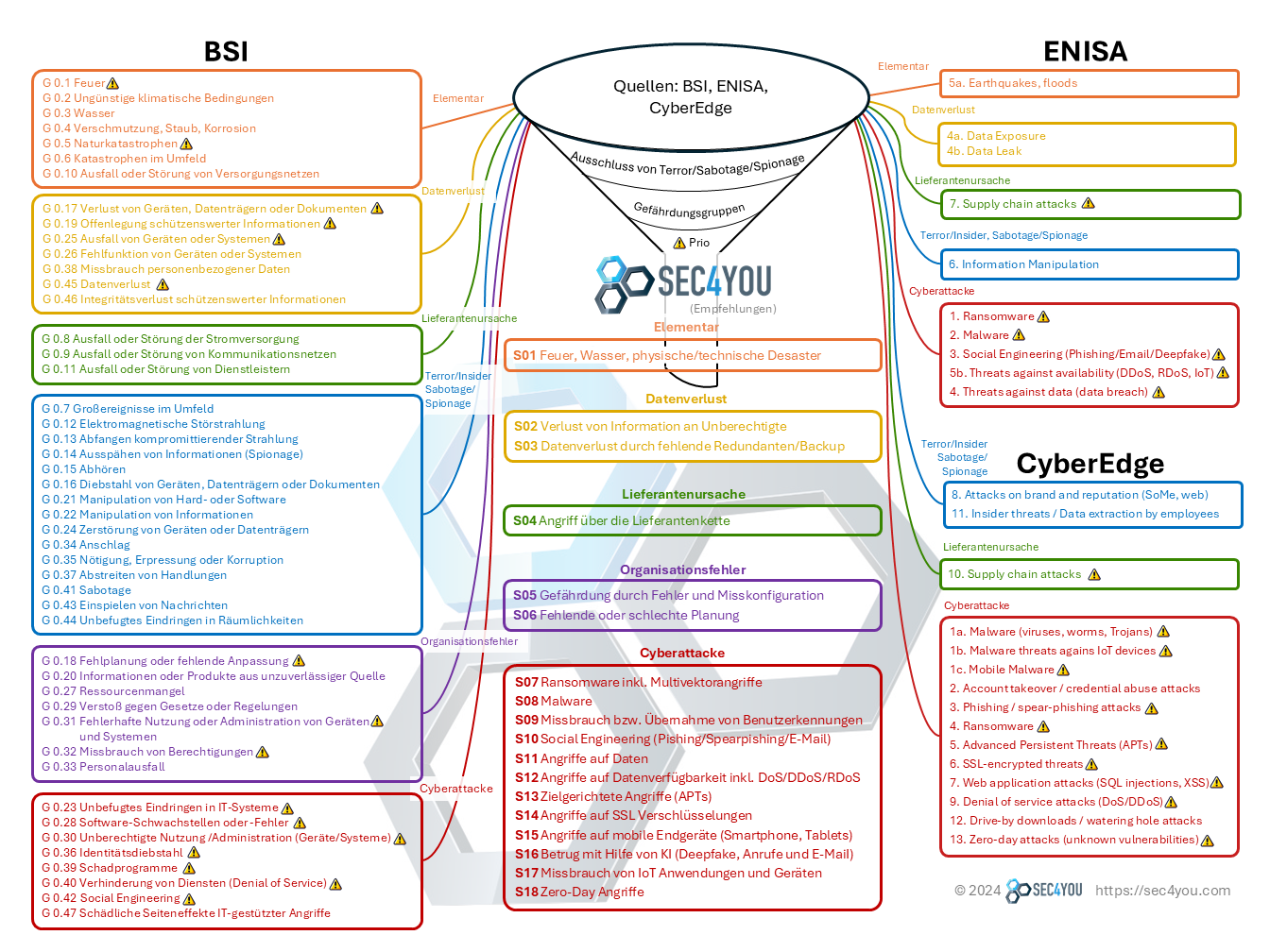
Als Grundlage für die SEC4YOU Informationssicherheits-Gefährdungsliste 2024 wurden folgende Quellen genutzt:

Die 47 Elementare Gefährdungen des Deutschen Bundesamt für Informationssicherheit (BSI)
Eine sehr klassische Liste, die eine Vielzahl an Elementargefahren auflistet und sich intensiv mit den Aspekten Sabotage/Terror und Spionage beschäftigt. Leider werden in dieser Veröffentlichung die modernen Cyberangriffsvektoren nicht ausreichend bewertet.

ENISA Threat Landscape 2024
Eine wertvolle Bewertung der Informationssicherheit der Europäischen Agentur für Cybersecurity die auf 130 Seiten die Cybersecurity Trends analysiert und hierbei die wesentlichsten sieben Gefährdungen beschreiben und detaillierte Empfehlungen zur Vermeidung geben.

2023 Cyberthreat Defense Report der CyberEdge Group
Dieser Report beleuchtet Technologien und deren Resilienz gegen Cybergefahren, zusätzlich bietet der Report eine ausgezeichnete Bewertung von 13 Cybergefahren die in keiner Risikobeurteilung fehlen dürfen.
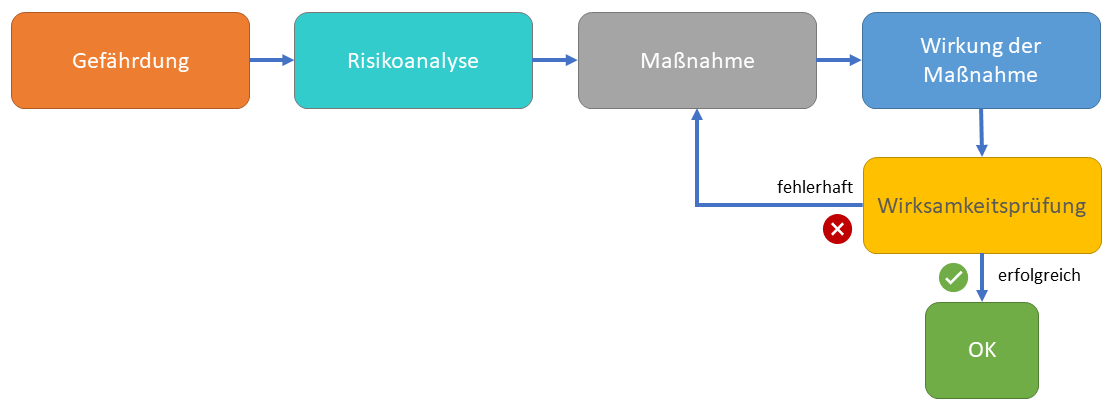
Klare Unterscheidung zwischen Gefährdung, Maßnahme, Wirkung und Wirksamkeitsprüfung
In einer Informationssicherheitsrisikobeurteilung ist der CISO gefordert tatsächlich die Gefahren/Gefährdungen zu bewerten und erst später die Maßnahme und deren mögliche Wirkung festzulegen, hier an einem vereinfachten Praxisbeispiel „Malware“ die Abgrenzung der Begriffe:
- Gefährdung: Die Gefahr, dass das Unternehmen von Malware infiziert wird.
- Maßnahme:
- Flächendeckende Malware-Schutzsoftware auf allen Endgeräten mit Hersteller A
- Perimeter Gateway-Schutz und Upload-Filter mit Hersteller B
- Regelmäßige Prüfung interner und externer Dienste auf Schwachstellen (Vulnerabilities)
- Wirkung der Maßnahme (die Definition der Wirksamkeitsziele):
- Malware aus der Quelle Internet und E‑Mail wird zuverlässig am Gateway erkannt.
- Malware aus der Quelle USB-Sticks und Ende-zu-Ende verschlüsselten E‑Mails wird zuverlässig am Endgerät erkannt.
- Wirksamkeitsprüfung:
- Gibt es Indizien, dass Malware am Gateway, Upload-Filter oder Endgeräten nicht zuverlässig erkannt werden?
- Wird Malware auch in verschlüsselten Verbindungen erkannt?
- Sofern in der Wirksamkeitsprüfung festgestellt wird, dass die Maßnahme die Wirksamkeit nicht erfüllen, müssen die Maßnahmen optimiert oder erweitert werden.
Dieser Artikel widmet sich nur der Auswahl der Gefährdungen für Ihr IT-Risikomanagement. Die Bewertung der Risiken und Auswahl von Maßnahmen findet nach der Erstellung der Gefährdungsliste statt. Eine passende Methode finden Sie in unserem Online Shop unter: Vorlage InfoSec Risikomanagement Methode gemäß ISO 27001
Die SEC4YOU Methodik
Wir haben die Gefährdungen der drei Quellen (1) die Elementaren Gefährdungen des BSI, (2) den ENISA Threat Landscape 2024 Report und (3) den CyberEdge 2023 Cyberthreat Defense Report erfasst und priorisiert. Die Priorität einer Gefährdung erkennen Sie in der Grafik unten an der gelben Markierung.
Dann haben wir die Gefährdungen in die folgenden Kategorien klassifiziert: Elementar, Datenverlust, Lieferantenursache, Terror/Insider/Sabotage/Spionage, Organisationsfehler, Cyberattacke
In einem Filter haben wir anschließend die priorisierten Gefährdungen aller 3 Quellen zusammengefasst, hierbei jedoch die Kategorie Terror/Insider/Sabotage/Spionage entfernt, weil für einen Großteil der Unternehmen diese Kategorie wenig relevant ist.
Das Ergebnis: Die SEC4YOU Informationssicherheits-Gefährdungsliste 2024
Die folgenden 18 Bedrohungen wurden als die wesentlichsten Gefahren für den IT-Betrieb erarbeitet:
Elementar
- Feuer, Wasser und andere physische/technische Desaster inkl. Stromausfall
Datenverlust
- Verlust von Informationen an Unberechtigte (physisch und elektronisch)
- Datenverlust durch fehlende Redundanzen/Backup
Lieferantenursache
- Angriffe über die Lieferantenkette
Organisationsfehler
- Gefährdung durch Fehler oder Misskonfiguration
- Fehlende oder schlechte Planung
Cyberangriffe
- Ransomware inkl. Multivektorangriffe
- Malware
- Missbrauch bzw. Übernahme von Benutzerkennungen
- Social-Engineering (Phishing, Spear-Phishing, weitere E‑Mail Angriffe)
- Angriffe auf Daten
- Angriff auf die Datenverfügbarkeit inkl. DoS/DDoS/RDoS
- Zielgerichtete Angriffe (APTs)
- Angriffe auf SSL/TLS Verschlüsselungen
- Angriffe auf mobile Endgeräte (Smartphone, Tablets)
- Betrug mit Hilfe von KI (Deepfake, Anrufe und E‑Mail)
- Missbrauch von IoT Anwendungen und Geräten
- Zero-Day Angriffe
Erklärung zu der Gefährdungssliste
S01 Feuer, Wasser und andere physische/technische Desaster
Hierbei geht es um Naturkatastrophen und lokale Elementargefahren, wie Feuer oder Wasser die IT-Infrastrukturen zerstören können. Jedoch auch technische Defekte in Serverräumen oder an kritischen IT-Diensten die einen IT-Betrieb vollständig unterbrechen. Egal ob Hochwasser, ein Brand oder der Löschschaum das Server-Rack zerstört, sorgen sie rechtzeitig für Redundanzen und mehrfache Datenhaltung.
S02 Verlust von Informationen an Unberechtigte (physisch und elektronisch)
Bei dieser Gefahr geht es um die Informationen selbst. Jedoch ist es unerheblich, ob eine unberechtigte Person diese als Papierdokumente entwendet, oder diese über einen Fernzugriff elektronisch kopiert werden. Gelangen unternehmenskritischen Informationen in die Hände eines Mitbewerbers, kann der Informationsverlust oder der Reputationsverlust dem Unternehmen nachhaltig schaden.
S03 Datenverlust durch fehlende Redundanzen/Backup
Sofern kritische IT-Dienste nicht redundant ausgelegt sind (u.a. Storage, Virtualisierungsplattformen, Domain Controller, Verzeichnisdienste, DNS-Server, Web-Dienste) kann es zu Datenverlusten kommen. Hierbei können sowohl Hardwaredefekte als auch Konfigurationsfehler oder einfach menschliche Fehler die Ursache für einen Datenverlust sein. Schlussendlich hilft eine fachmännisch geplante und regelmäßig getestete Backup-Lösung vor Datenverlust.
S04 Angriffe über die Lieferantenkette
Bei der „Supply-Chain-Attack“ wird das Vertrauen zwischen einem (großen) Lieferanten und seinen Kunden missbraucht. Hier können Angreifer über eingerichtete Fernzugriffe oder beim Lieferanten hinterlegte Credentials bzw. Schlüssel die Daten und Systeme eines (oder vieler) Unternehmen kompromittieren. In der Vergangenheit wurden jedoch ein Großteil der Angriffe über kompromittierte Software einzelner Lieferanten durchgeführt, wo Hacker gezielt Angriffsmethoden in vermeintlich vertrauenswürdige Software-Updates platzieren konnten.
S05 Gefährdung durch Fehler oder Misskonfiguration
Speziell durch fehlende Konfigurationsvorgaben (Hardening-Guidelines, Configuration-Baselines) und auch durch fehlende Automatisierungen werden Server und IT-Dienste unterschiedlich und z.T. unsicher konfiguriert. Auch werden nachträgliche sicherheitsrelevante Konfigurationsanpassungen durch die IT-Teams von Unternehmen oft nicht umgesetzt. Leider allzu oft werden Software oder Dienste mit den Standard-Konfigurationen und Default-Zugangsdaten in Betrieb genommen, was von Angreifern einfach ausgenutzt werden kann.
S06 Fehlende oder schlechte Planung
Mangelhaft geplante IT-Infrastrukturen, unsachgemäße Wartungs- und Reparaturprozesse, unterschätzte IT-Migrationen, Beschaffung von IT-Systemen mit unzureichenden Sicherheitseigenschaften, schlechte Ressourcenplanung, fehlende Ersatzteile und auch veraltete Übertragungsprotokolle sind auf fehlende Planung und mangelhaftes Projektmanagement zurückzuführen. Nur durch frühzeitige Berücksichtigung der Informationssicherheit und stringentes Planungsmanagement werden informationssicherheitsrelevante Projekte aufgedeckt und können der Kritikalität entsprechend geplant und umgesetzt werden.
S07 Ransomware inkl. Multivektorangriffe — UPDATE
Ist eine spezielle Art eines hinterhältigen Angriffes bei dem Angreifer die Unternehmensdaten verschlüsseln und Lösegeld verlangen, um die Daten wieder zugänglich zu machen. Manchmal stehlen die Angreifer auch die Daten und verlangen Zahlungen damit die Daten nicht an Behörden, Wettbewerber oder die Öffentlichkeit geschickt werden. Bei den Eintrittstoren für Ransomware stehen Phishing Emails und Remote Desktop Protokoll (RDP) Verbindungen an oberster Stelle. Neu hinzugekommen sind Multivektorangriffe, hier wird während der Erpressungszeit auch ein (D)DoS Angriff gestartet oder es erfolgt eine Anzeige bei der Datenschutzbehörde durch die Erpressergruppe, um den Druck auf das Unternehmen zu erhöhen das Erpressungsgeld zu zahlen.
S08 Malware
Malware ist der Überbegriff für Software, Firmware oder Code der in böswilliger Absicht die Vertraulichkeit, Integrität oder Verfügbarkeit von Systemen beeinflusst. Zu den Unterformen zählen Viren, Würmer, Trojanische-Pferde, RATs (Remote-Access-Tools) und Code-infektionen von Systemen. Auch zählen manche Spyware und Adware zu Malware. Eine guter Malware-Schutz mit Verhaltensanalyse zur Laufzeit auf allen Systemen (Clients, Server, Gateways) hilft die Infektion und Verbreitung von Malware einzudämmen. Installation von Software und Treiber durch BenutzerInnen auf Endgeräten sollte massiv eingeschränkt sein.
S09 Missbrauch bzw. Übernahme von Benutzerkennungen
Beim Missbrauch von Benutzerkennungen bzw. Identitätsdiebstahl täuscht der Angreifer die Identität einer Person vor, um in deren Namen aufzutreten. Dies gelingt besonders einfach, indem man E‑Mail Konten hackt und dann über emailbasierte Passwort-Reset Verfahren weitere Dienste übernimmt. Für diese Gefährdung sind starke Passwörter mit zusätzlicher Zwei-Faktor-Authentifizierung der beste Schutz. Gleichzeitig müssen Unternehmen die BenutzerInnen über Security-Awareness Kampagnen bezüglich der Nutzung von einzigartigen Passwörtern und der Gefahr durch Phishing-Angriffe schulen.
S10 Social-Engineering u.a. Phishing, Spear-Phishing, weitere E‑Mail Angriffe
Die Varianz bei Gefährdungen durch Social-Engineering ist groß und inkludiert Pishing, Spear-Phishing, Whailing, Smishing, Vishing und in Zukunft sicher auch Video-Phishing mit Deep-Fake Technologie. Hierbei nimmt das Infektionsmedium E‑Mail immer noch die größte Rolle ein. Unternehmen sind angehalten die perfiden Methoden von Social-Engineering Angriffen über aktuelle Beispiele und deren möglichen Auswirkungen in regelmäßigen Security-Awareness Kampagnen und verpflichtenden Schulungen mit allen MitarbeiterInnen zu trainieren.
S11 Angriffe auf Daten
Zu den Gefahren durch Angriffe auf Daten zählen unter anderem der unberechtigte Zugriff, unerwünschte Veröffentlichung, falsche Berichtserstattung, Falschinformation und Desinformation, beim Letzteren handelt es sich um die Verbreitung bewusst falscher Informationen zum Zwecke der Täuschung. Oft werden diese Vorfälle als Datenpanne / Data-Breach / Data-Leak bezeichnet und beziehen sich immer auf die Veröffentlichung sensibler, vertraulicher oder geschützter Daten in einer nicht vertrauenswürdigen Umgebung. Besondere Kritikalität entsteht, wenn der Data-Breach personenbezogene Daten gemäß der DSGVO betrifft. Dann muss das Unternehmen diese Datenpanne gegenüber der Behörde anzeigen.
S12 Angriff auf die Datenverfügbarkeit inkl. DoS, DDoS, RDoS — UPDATE
Bei den Angriffen gegen die Datenverfügbarkeit stehen zwei Angriffsmethoden im Vordergrund: Distributed Denial of Service (DDoS) und Angriffe auf Web-Dienste. Ein DoS/DDoS Angriff blockiert kritische IT-Dienste des Unternehmens vollständig, dies können der Internet-Uplink, die E‑Mail-Serverdienste, Außenstellenanbindungen oder beliebige andere Dienste wie der Online-Verkauf sein. Wird darüber hinaus von den betroffenen Unternehmen Lösegeld gefordert, spricht man von einem Ransom Denial of Service (RDoS) Angriff. Bei den Web-basierten Angriffen wird in der Regel die Datenintegrität und Verfügbarkeit adressiert. Hierbei können auch durch manipulierte Web-Links unscheinbare Web-Dienste für die Verteilung von Malware oder für den Diebstahl von Web-Form Daten missbraucht werden.
S13 Zielgerichtete Angriffe (APTs)
Der große Unterschied zwischen einem „normalen“ Hacker-Angriff auf eine Infrastruktur und einem Advanced Persistent Threat (APT) ist, dass APT-Angriffe sehr zielgerichtet sind und mit einem hohen Aufwand durchgeführt werden. Hierzu recherchieren die Angreifer teilweise wochenlang die Mitarbeiterverantwortlichkeiten und bestehende Kunden- und Lieferantenbeziehungen bevor der Angriff gestartet wird. Auch wird für einen APT-Angriff oft individuelle Malware entwickelt, die von handelsüblichen Malware-Schutzprogrammen nicht erkannt wird. Oft sind APT-Angriffe primär auf das langfristige Ausspähen der Opfer ausgelegt (Link: Industrie-Spionage).
S14 Angriffe auf SSL/TLS Verschlüsselungen
Bei den Angriffen auf SSL/TLS Verschlüsselung geht es zum einen um die Gefahr durch selbstsignierte Zertifikate, die einfach per Man-in-the-Middle angegriffen werden können und zum anderen um veraltete, unsichere Kryptographie-Algorithmen und Schlüssellängen, die keinen ausreichenden Schutz für Übertragungsprotokolle bieten. Speziell der Einsatz von OpenSSL in Anwendungen und Web-Diensten birgt größere Gefahren, da OpenSSL Verwundbarkeiten (siehe Heartbleed, Poodle) umfassend dokumentiert werden und Angreifer diese unverzüglich auszunutzen versuchen.
S15 Angriffe auf mobile Endgeräte (Smartphones, Tablets) — NEU
Wenn mobile Geräte mit Schadsoftware infiziert werden, kann dies mehrere Auswirkungen haben. Beim Automated Transfer Systems (ATS) versuchen Angreifer mit Mobile – Banking – Trojanern nicht autorisierte Geldtransfers durchzuführen bzw. Kontrolle über die Hardware zu erlangen. Telephone – based Attack Delivery (TOAD) nutzen Social Engineering Methoden, um an persönliche Daten zu kommen (Personally Identifiable Information), Konten zu übernehmen (Account TakeOver) oder um mobile Schadsoftware zu installieren.
S16 Betrug auch mit Hilfe von KI (Deepfake, Anrufe, E‑Mail) — NEU
Im Vorfeld sammeln Angreifer öffentlich zugängliche Daten über ihre Opfer, etwa aus sozialen Medien oder beruflichen Netzwerken. Mit Hilfe dieser Daten wird anschließend auch generative KI genutzt, um maßgeschneiderte Emails zu erstellen, die die Betroffenen zur Preisgabe sensibler Daten bringen soll. Mittlerweile ist die Deepfake Technologie so weit fortgeschritten, dass es Angreifern gelingt, sich in Live-Meetings oder Telefonaten für bekannte Personen auszugeben. Auf diese Weise gelingt es Ihnen, die Opfer zur Überweisung hoher Geldbeträge zu bewegen.
S17 Missbrauch von IoT Anwendungen und Geräten — NEU
Die rasche Verbreitung von IoT-Geräten (Internet of Things) in Büros, Fabriken, Wohnungen, Fahrzeugen und sogar in Versorgungs- und Verkehrsnetzen ganzer Städte bringt eine Vielzahl neuer Bedrohungen mit sich. Diese Geräte kommunizieren über das Internet und werden häufig durch Cloud-Lösungen gesteuert. Dabei kommen oft modulare Dienste zum Einsatz, die auf Application Programming Interfaces (APIs) angewiesen sind. APIs geraten zunehmend ins Visier von Angreifern, da sie aufgrund fehlerhafter Implementierungen oder mangelnder Sicherheitsmaßnahmen eine ernstzunehmende Angriffsfläche bieten.
S18 Zero-Day Angriffe
Im Prinzip ist eine Zero-Day Verwundbarkeit eine von vielen Schwachstellen, die entdeckt werden, jedoch mit dem Unterschied, dass es für die Schwachstelle noch keinen Patch oder Hotfix gibt. In einer frühen Phase einer Zero-Day Verwundbarkeit liegen oft auch noch keine fundierten Informationen über das Ausmaß und Auswirkung der Schwachstelle vor. Unternehmen sind gefordert solche Zero-Day Verwundbarkeiten frühzeitig zu erkennen, hierzu wird eine zuverlässige Zero-Day Informationsquelle benötigt und eine schnelle Bewertung ob betroffene Dienste im Unternehmen eingesetzt werden.
Klassifizierung: PUBLIC TLP:CLEAR
Ersteller: Andreas Schuster, SEC4YOU
Version: 2.0
Datum: 23.11.2024