PENETRATION TEST / PENTEST OR INTERNET SECURITY SCAN?

An Internet Security Scan or Internet Penetration Test (PenTest for short) should be carried out regularly in order to identify and eliminate vulnerabilities and potential risks in a timely manner and thus minimize the risk of a successful hacker attack.
The tests are offered in blackbox and whitebox versions. Blackbox means that no information beyond the IP addresses or domains to be tested is provided. With Whitebox, on the other hand, relevant information about the relevant infrastructure is made available before the test begins, and there is ongoing coordination with the client. This increases the efficiency of the resources used and the level of detail of the results.
BSI standardized PenTest
The test is carried out on the basis of the implementation concept for penetration tests of the German Federal Office for Information Security (BSI). This ensures a structured and methodical procedure with comprehensible results.
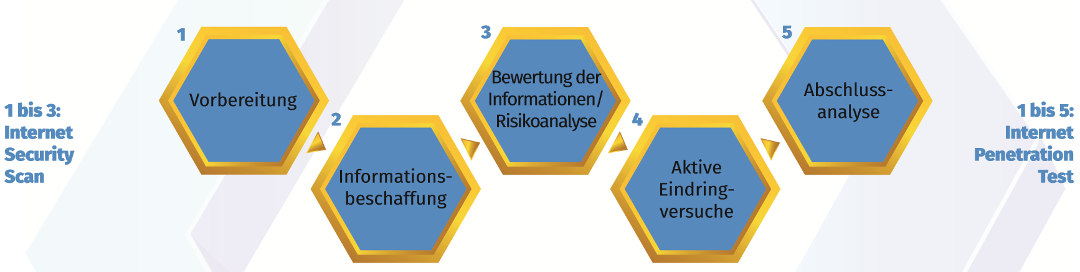
Phase 1: Preparation
Definition of the IP address ranges or Internet domains to be tested and the organizational framework conditions as well as the selection of the testing approach (white or black box).
Phase 2: gathering information
Procurement of all publicly available information about the infrastructure to be tested. In the case of a whitebox test, the information provided by the client is also taken into account. Internet Security Scan and Web Application Security Scan of authorized IP addresses and websites.
Phase 3: Evaluation of the information / risk analysis
Analysis and evaluation of the identified vulnerabilities and risks. Identification of systems and applications where potential attack points have been identified (as a target for phase 4).
The results of phase 3 are documented in the form of a technical report and submitted to the client (not for black box).
Phase 4: Active penetration tests
Based on the technical report of phase 3, targeted attempts are made to exploit the potential vulnerabilities (penetration test) in order to gain unauthorized access to data or systems.
Phase 5: Final analysis
During the final analysis, the results of the test execution are evaluated with regard to potential risks (low, medium, high) and concrete recommendations are developed to mitigate them.
The results of the PenTest or Internet Security Scan are documented in the form of a test report consisting of a management summary and a detailed technical description.
Enjoy the certainty that you have actively taken important steps for your own IT security!
DATASHEET
YOUR ADVANTAGES
- Detect vulnerabilities in your IT before they are exploited.
- Optimal combination of automated tests and manual penetration tests by our IT security specialists.
- Risk assessment of the vulnerabilities found
- The final report includes a management report and detailed descriptions of the identified vulnerabilities as well as appropriate recommendations for action.
You want further information?
